SMB protocol commonly known as Server Message Block protocol has been a hot target among threat actors for many years because of its complexity and open nature. This protocol was prone to plethora of attacks from SMB Null Sessions to Eternal Blue. It is the reason we are about to cover all things related to SMB Enumeration and go in-depth with Nmap SMB Scripts also known as the Nmap Scripting Engine (NSE).
However, SMB has covered a long journey in terms of its security hardening. It has been updated and improved to newest security standards in recent Windows Operating System releases. Latest SMB version is SMBv3.1 in Windows 10 and Windows Server 2016, while most vulnerable was SMBv1 in Windows XP and Windows Server 2003.
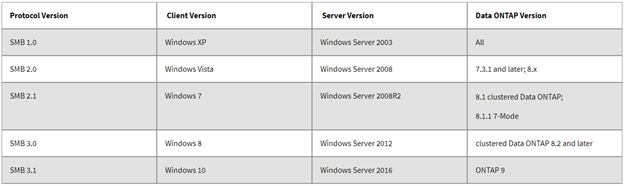
Because of it’s not so “Secure” history, it’s always been a go-to protocol for any threat actor or ethical hackers. With tools like the Nmap SMB Scripts it makes it even easier for attackers to perform SMB Enumeration. And also, it’s not surprising that we still have legacy End Of Life (EOF) operating systems running in various public and private sector organizations.
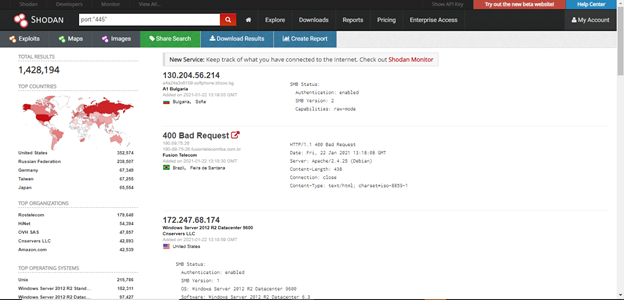
A quick query in Shodan confirms that there are 1,428,194 publicly accessible SMB ports and as it can be easily conceived that not everyone will be doing their housekeeping, lefts many of them a hot target to attack.
Why SMB Enumeration is important?
SMB is used to communicate over TCP/IP in a network. It is a client-server protocol used for file sharing, printers, serial ports and other resources on a network.
SMB can allow other applications and users to access files or execute command on a remote server. A client application can read, write and execute files on the server depending upon the configuration of the SMB share.
Port for smb is 445 while 135-9 ports are used for RPC calls which are essential for remote management of Windows systems.
It is essential to keep the target we are achieving before enumerating any service. So in this particular case we will be getting system information, Null sessions, open shares and CVEs like Eternal Blue from this service. These open shares might include some sensitive information like Username, Password, Hashes, Keys, TGS etc. which can be used further in the process. So to conclude, as per my knowledge we enumerate SMB for below purposes:
- Null Sessions
- Open Shares
- CVEs (Eternal Blue, Eternal Romance etc)
- System Information
Tools to enumerate SMB:
Now that we have the importance and common usage of SMB, let us discuss how we can enumerate it and look for any potential vulnerabilities that can be exploited. We will be using various tools for that purpose:
- Nmap SMB Scripts
- SMBmap
- Rpcclient
- Nbtscan
- Enum4Linux
NMAP SMB Scripts:
Network MAPper abbreviated as “nmap” is a common tool used by security professionals for reconnaissance purposes on network levels and is one of the reasons that Nmap was included as part of The Top 10 Best Penetration Testing Tools By Actual Pentesters. Nmap natively comes with its scripting engine, which has tons of open source scripts including those Nmap SMB scripts. Discussing all of scripts is out of scope of this article and we will be only leveraging NSE (Nmap Scripting Engine) to enumerate SMB.
There are 35 Nmap SMB scripts as part of the NSE. We will be going through the most common ones only in this article. While complete list can be seen using below command and can be used on need basis:
cd /usr/share/nmap/scripts; ls | grep smb

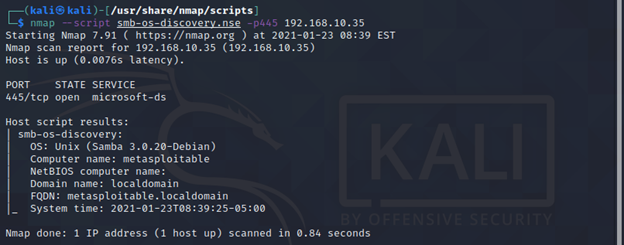
smb-os-discovery
It is used to enumerate the Operating System of target system along with other interesting things like:
- Computer name
- Domain name
- Forest name
- FQDN
- NetBIOS computer name
- NetBIOS domain name
- Workgroup
- System time
Command:
nmap --script smb-os-discovery.nse -p445 <target>
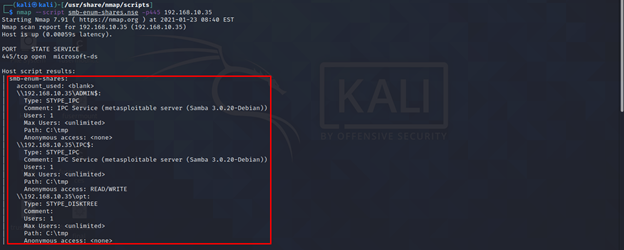
smb-enum-shares
It will enumerate publically exposed SMB shares, if available. In addition, if nmap is not able to get shares from any host it will bruteforce commonly used share names to check if they are accessible.
Command:
nmap --script smb-enum-shares.nse -p445 <target>
smb-enum-users.nse
As name suggests, it is used enumerate all users on remote Windows system using 2 different techniques.
- SAMR Enumeration
- LSA Bruteforcing
More can be read about the differences here.
Command:
nmap –script smb-enum-users.nse -p445 <target>
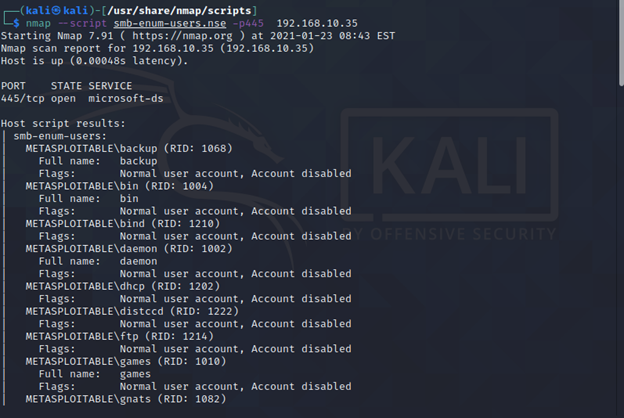
SMB Blanket Command for Enumeration:
We can run all SMB enumeration scripts in on go by following command.
Command:
nmap --script smb-enum-domains.nse,smb-enum-groups.nse,smb-enum-processes.nse,smb-enum-services.nse,smb-enum-sessions.nse,smb-enum-shares.nse,smb-enum-users.nse -p445 <target>
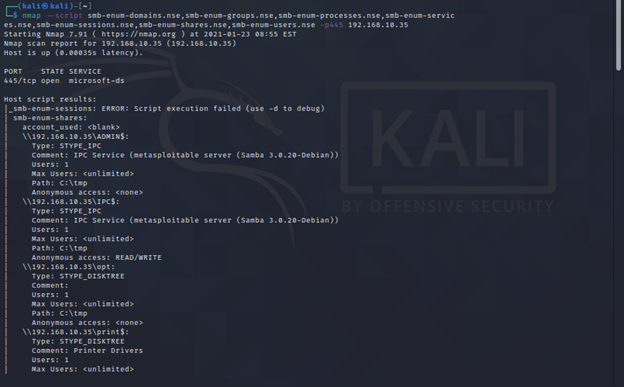
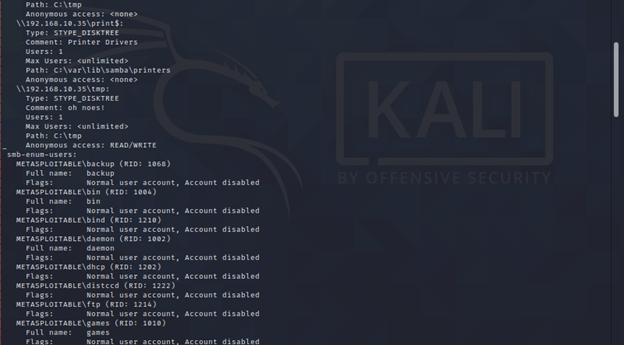
SMB Blanket Command for Vulnerability Detection:
By design, nmap comes with various scripts that can be used to detect various vulnerabilities or CVEs. Specifically for SMB, we can use nmap to detect below CVEs:
- 2009-3103
- 2017-7494
- ms06-025
- ms07-029
- ms08-067
- ms10-054
- ms10-061
- ms17-010 (Eternal Blue)
All these vulnerabilities can be detected using single nmap command.
Command:
nmap --script smb-vuln-conficker.nse,smb-vuln-cve2009-3103.nse,smb-vuln-cve-2017-7494.nse,smb-vuln-ms06-025.nse,smb-vuln-ms07-029.nse,smb-vuln-ms08-067.nse,smb-vuln-ms10-054.nse,smb-vuln-ms10-061.nse,smb-vuln-ms17-010.nse,smb-vuln-regsvc-dos.nse,smb-vuln-webexec.nse -p445 <target>
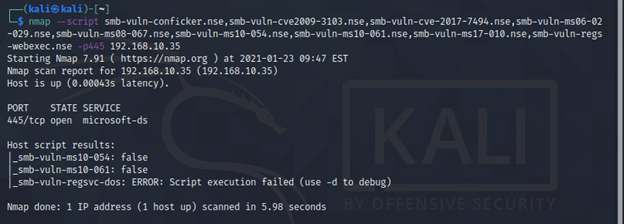
Key Features:
NMAP is a great tool when it comes to enumerate ports and SMB is not exception. Due to its high optimization capacity NMAP gives you pretty high control on every TCP/UDP packet you send towards the target.
In particular, to SMB, because of it scripting engine i.e. NSE nmap can be used to retrieve a great deal of information from remote host. Not just retrieving information from the remote host, it has few scripts that can check on runtime that if any particular service is vulnerable to preconfigured CVEs or not. It comes really handy when scanning multiple hosts on large scale.
SMBmap:
SMBmap is go-to tool for every penetration tester or ethical hacker when it comes to enumerating SMB. While it comes pre-installed in Kali Linux it can be installed from here. It is one for all tool and does pretty much everything in terms of enumeration from listing shared drives, permissions to executing remote commands
We will be discussing various commands with their use cases.
Commands:
smbmap -H <IP>
-H host
-P (optional) port number
This command will enumerate SMB as an unauthenticated user.
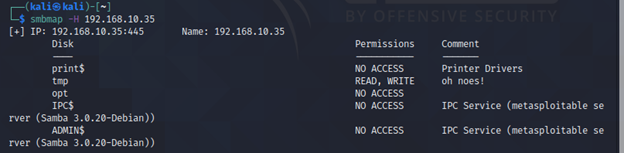
smbmap -u "user" -p "pass" -H <IP>
-u username
-p password
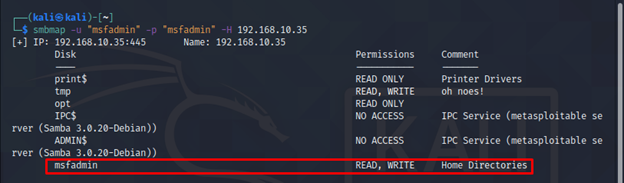
It will enumerate SMB as an authenticated user and will give information particular to that user on SMB. You will notice additional “msfadmin” share.
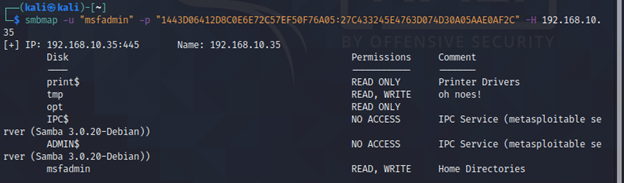
smbmap -u "username" -p "<NT>:<LM>" -H <IP>
We can also use NTLM hashes to authenticate ourselves over SMB using smbmap by this command.
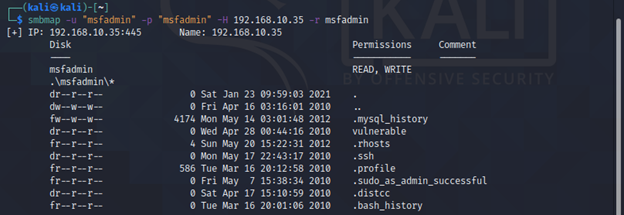
smbmap [-u "username" -p "password"] -r [Folder] -H <IP>
-r Non Recursive listing
For Non Recursive listing of folder this command will be used.
smbmap [-u "username" -p "password"] -R [Folder] -H <IP>
-R Recursive Listing
As you have already guessed, this command will be used for Recursive listing of any folders over SMB.
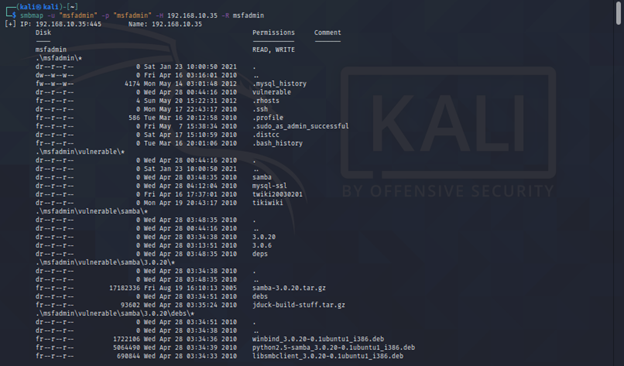
sudo smbmap -R Folder -H <IP> -A <FileName> -q
-A specifying the filename to search
-q for quiet verbose output
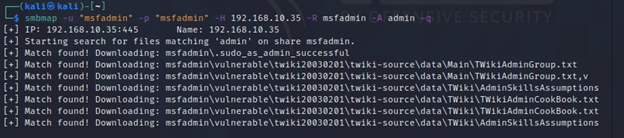
Key Features:
If we want to map whole SMB port in every aspect, then SMBmap is the only tool that every security practitioner will recommend. It’s powers are endless, from listing the publically exposed shares, downloading them and searching for specific keywords in those file SMBmap does all of it.
It can also be used to execute commands with “-x” flag once authenticated. Natively SMBmap stores all the downloaded files in /usr/share/smb.
RPCclient
RPCclient is a remote windows utility, which can be used to query MS-RPC for various commands. It was essentially build to test MS-RPC. Because of its remote use, it has been used by many developers to query Windows NT system from UNIX like systems.
It has plethora of commands to query which cannot be discussed in this article alone. We will be going through only basic commands here.
Commands:
rpcclient -U "" -N <IP>
-U username
-N IP of the host

It is a classic Null Session Command where username flag is essentially “Null”.
rpcclient //hostname -U domain/<username>%<NTLM hash> --pw-nt-hash
–pw-nt-hash used to specify the format of credentials
Once we are connected to the remote MS-RPC service either through null session or through, supplied credentials then we can run various command to MS-RPC to retrieve information from remote host. Some of commands that can be used are given below:
| Command | Purpose |
| queryuser | Retrieve user information |
| querygroup | Retrieve group information |
| querydominfo | Retrieve domain information |
| enumdomusers | Enumerate domain users |
| lookupsids | Look up SIDs to usernames |
| lsaaddacctrights | Add rights to a user account |
Key Features:
As name suggest RPCclient is a client for Windows MS RPC service and used to query that service. If you want to manually enumerate SMB port then RPCclient is for you. Firstly we have to authenticate user either through known username and passwords or using NULL session.
Once we are authenticated, we can use several commands to query for specific information we need. Some of these are shown above while a complete list can retrieved using “-h” flag.
nbtscan
When it comes to scanning your entire network for open shares, nbtscan comes in really hand. It is CLI utility that tries to scan open NetBIOS name servers in a remote or local network. It is built on top of Windows utility “nbtstat” and is able to scan whole subnet instead of individual IP, while individual IPs can also be done by using the right flags.
Command:
nbtscan -r 192.168.0.1/24
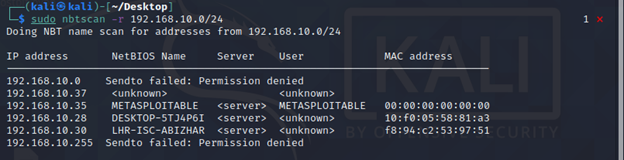
The numeric hexadecimal code and the “type” identifies the service type, for example a code of <20> highlights that the target is running file-sharing service.
Unfortunately, nbtstat only reports hexadecimal codes, we manually need to find the meaning of these hexadecimal codes.
Key Features:
Use case for nbtscan is very particular in nature i.e. we can scan whole range of subnet for Open File shares. It is a very practical tool that is very fast in doing a particular task i.e. finding open shares in whole subnet range.
It might not come in handy when doing CTFs or if you want to enumerate every aspect if SMB then it might be your priority but if you’re in a Pentest engagement and you have a pretty large scope of Windows Active Directory environment to cover then it should be your top choice, as it will provide low hanging fruits with speed which can be further used in your engagement.
Enum4Linux
Enum4Linux, a “noisy tool” as some suggests, is a compilation various other open source projects like rpcclient, smbclient, nmblookup etc. It is written in Perl and is a wrapper around earlier mentioned open source tools. A negative aspect of using Enum4Linux in our enumeration process is that, it throws over whelming amount of information in STD OUT as compared to other tools, which can be annoying some times. In addition, some of its plugins are outdated and throw errors.
Commands:
enum4linux -A <target>
-A Do all simple enumeration
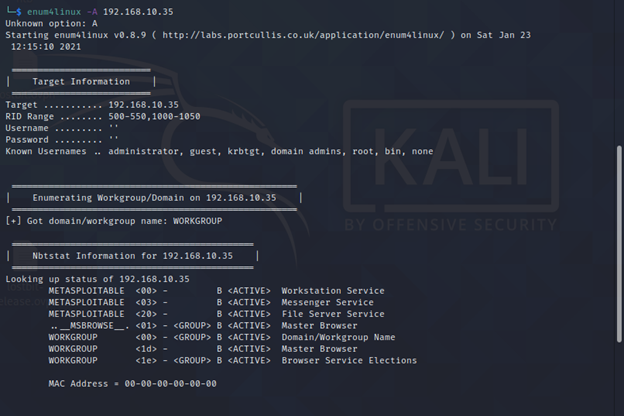
Key Features:
As stated earlier, it is a perl wrapper around various open source projects like rpcclient, nbtscan, nmblookup etc. so it has a unique mix capabilities of many tools. With its one command only it can be used to enumerate all information regarding SMB whether it be OS information, public shares, Workgroups, retrieving password policy etc.
But it’s one major disadvantage is that, some of its components are outdated now and throw exception error due to which it cannot be run with all cylinders on.
One more disadvantage is that, sometimes it throws redundant information that is not much of value and user has to filter the required results as per their need.
TL; DR
SMB is a very common protocol often used in Windows Environment in various public and private enterprises. It has a history of security vulnerabilities in earlier versions like SMBv1, SMBv2 and SMBv3, while current built SMBv3.1 is somewhat stable and built with security in mind.
We have gone through various tools used to enumerate SMB, while every tool has its own specific capabilities, as per the requirement of the deliverable and time constraints.
Out of all, NMAP scripting engine stands out the most when it comes to SMB vulnerability scanning on the go. It has in built scripts that can be used for various purposes from enumeration to VA scanning. Fast, reliable and highly optimizable tool to used when working with large scope.
When it comes to enumerating and exploiting SMB completely SMBmap is the tool you may need. It covers each and every aspect of SMB from listing file shares, uploading and downloading files, using Null sessions, authentication via hashes and executing remote system commands.







 Best Ethical Hacking Books for Beginners to Get Started
Best Ethical Hacking Books for Beginners to Get Started





