A firewall is a security device that screens incoming and outgoing traffic through a network. A firewall also allows specific types of traffic to pass through while blocking the other, with the help of specific predefined rules. It establishes a barrier between the network and the traffic from the outside world. As a result, the barrier protects the network from viruses and malicious entities by screening through the incoming traffic. One must properly understand stateful vs stateless firewalls if they wan to protect their system.
A firewall is an essential line of defense in terms of the security of the network. Beyond the router, the main thing securing the network perimeter is a firewall. The firewall filters the potentially harmful or dangerous incoming traffic that may establish a threat, i.e., trojans, viruses, etc. A firewall is dependent on a bunch of rules about the kinds of traffic and allowed source or destination. The firewalls used at first, i.e., in the early 1990s, included many straightforward principles that control external access to an organization’s resources. A packet filtering system was created that disposes of network packets by analyzing the data it contains (i.e., source and destination address, port number, etc.). While viable at that point, these firewalls eventually evolved into more modern ones.
“Stateful” Firewalls:
New Firewalls, known as “stateful” firewalls, end up being a significant jump forward. These firewalls had the option to hold data packets until sufficient data was accessible to make a judgment about their state. A couple of years later, a bit of innovation in these firewalls was a “connection state” rule that made filtering easier since knowing whether the data packet was part of an existing connection or not, but this can result in DDOS attacks. In other words, fake connection packets can override the data packets. The Firewall Toolkit (FWTK) was created in 1994 to overcome this obstacle. This third era of firewalls can determine whether the communication protocol is abused or not.
Similarly, this application-layer separating permitted the firewall to see how FTP and HTTP work and adapt accordingly. The same application-level packet filtering concept is behind modern firewalls as well. However, there is more spotlight on deep-packet examination.
Types of Firewalls: Stateful vs Stateless
Packet filtering firewalls:
This kind of firewall deploys checkpoints at the router or a switch checking the packets coming through. It allows or denies the data packet by checking basic information like source and destination IP address etc., instead of thoroughly checking the data packet.
Circuit-level gateways:
These are the simplest types of firewalls that check for a packet’s legitimacy by verifying the TCP handshake, not caring about whatever is inside the data packet. Circuit level gateways use significantly less amount of computing power.
Stateful inspection firewalls:
In order to make the level of security a bit higher than the previous two firewalls, these kinds of firewalls check for both TCP handshake and the data inside the data packet. Stateful inspection firewalls use more computing power than circuit-level gateways.
Proxy firewalls:
These kinds of firewalls set off at the application layer as barriers between incoming traffic sources and the network. Proxy firewalls work on the same technique that stateful inspection firewalls do, but it does perform inspection checks at an intense level. After inspecting the packet thoroughly and making sure it doesn’t contain malware, it allows it to move forward, making it a very reliable firewall.
Software Stateful vs Stateless Firewalls:
Any firewall installed on a device itself instead of another separate hardware like a cloud server is called a software firewall. These are one of the most powerful firewalls and as difficult and time-consuming to be deployed. By separating individual network endpoints from each other, software firewalls can be a powerful tool for security.
Cloud firewalls:
A cloud can also deliver a firewall. In this instance, the result is a cloud firewall. As the need grows, users can maximize the cloud server’s capacity to manage substantial traffic loads.
Stateful firewalls:
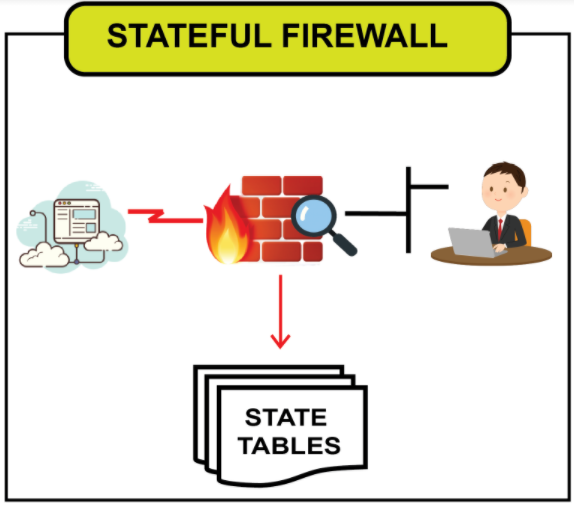
Stateful means that the thing is holding the state alone (perhaps in memory ), but that doesn’t imply that the state can not be backed in a database. The stateful firewalls screen the entire state of network connections and continually break down the total traffic and information packets setting, looking for a passage to a network instead of discrete traffic and data packets in isolation.
TCP-Based Handshake: Stateful vs Stateless
The stateful firewalls apply their approach depending on the connection state. Let’s look at the case of TCP-based handshake. In TCP, four pieces control the state of connection, i.e., SYN, ACK, FIN, and RST. When a connection starts through a 3-way handshake, the TCP shows the SYN banner. The firewall uses the banner to demonstrate the appearance of another connection. Then, the connection gets the SYN+ACK flag by the server. Until the client responds with ACK, the connection doesn’t build up. Like this, by looking at FIN+ACK or RST data packet, the connection is set apart for erasure not too far off alongside for future packets. After the firewall affirms a specific traffic type, the connection will attach to a state table and roam freely. The traffic which fails to complete the necessary handshake will no longer exist.
Another word for stateful firewalls is circuit-level firewalls. They work in the same way as stateless firewalls, but they come with a plus point as they can go one layer up at Layer 5, the session layer, compared to the stateless firewalls, which works at Layer 3 and Layer 4 only. This results in giving the firewall more flexibility and stronger security rules.
Stateless firewalls:
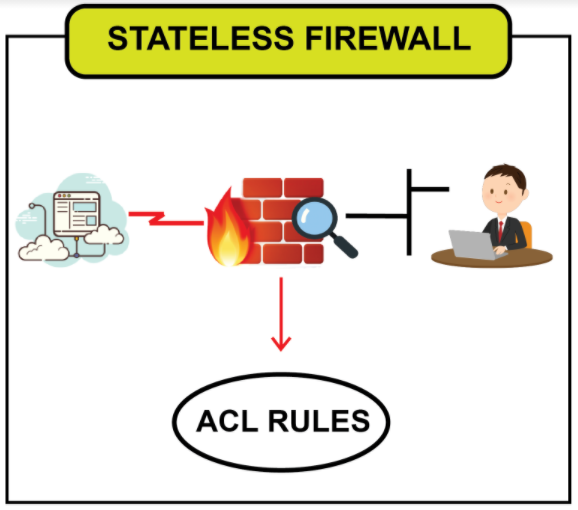
A stateless firewall is a packet filtering firewall that works on Layer 3 and Layer 4. These kinds of firewalls work on a set of predefined rules and allow or deny the incoming and outgoing data packets based on these rules. Stateless firewalls are less reliable than stateful firewalls on individual data packet inspection. Still, in case of defending a more powerful attack, it can be beneficial as it will block the attack by looking at the pattern. Stateless firewalls cannot differentiate between various network traffic, i.e., HTTP, HTTPS, FTP, SSH, etc. Let’s look at an example of setting up stateless firewalls using iptables.
PING: Stateful vs Stateless
Let’s ping on our machine using another computer system or a virtual machine.
cmd> ping 192.168.10.4
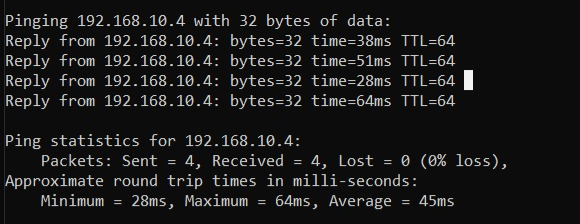
We can see that ping is successful, and the system has sent all the data packets. Now we will configure our firewall and modify its rules a bit so that it won’t accept ICMP packets again and ping can’t be successful.
ubuntu@ubuntu:~$ sudo iptables -A INPUT -p icmp -d 192.168.1.0/24 –icmp-type 8 -j DROP
Now let’s ping again.
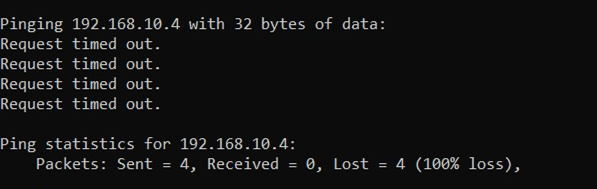
We can clearly see that the firewall has dropped all the commands..
We can check the default allowed traffic configured in the rules by using the following command
ubuntu@ubuntu:~$ iptables -L -n
Summary of Stateful vs Stateless Firewalls:
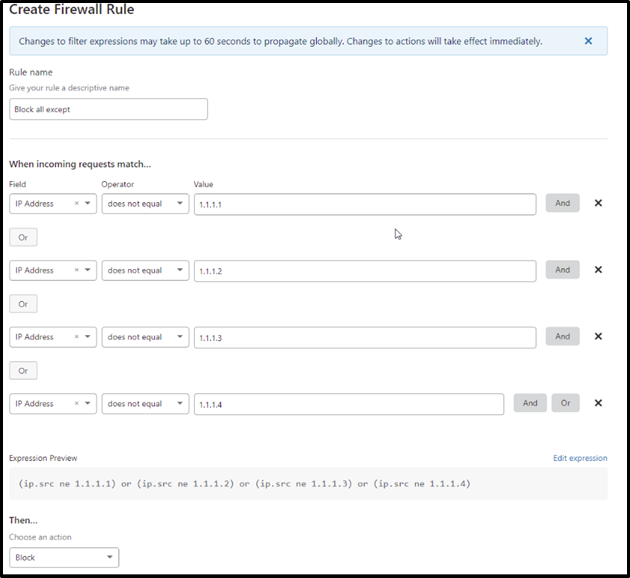
Indeed, a firewall is an essential line of defense in terms of network security. Monitoring the incoming and outgoing traffic and then allowing or blocking it is essential for every network. Stateless firewalls accept data packets depending on their origin i.e, IP address, port number, destination IP, etc. For example, the given rule will allow all SSH packets on port 22 from 192.168.10.x subnet.
-A INPUT -p tcp -s 192.168.1.0/24 -m tcp –dport 22 -j ACCEPT
The matching rule for ongoing packets would look like the incoming one.
-A OUTPUT -o eth0 -p tcp –sport 22 -j ACCEPT
Stateful firewalls accept the traffic depending on its state. The rule below will cause the packets on port 22 to be accepted upon the initiation of a new connection. The rule will also accept the packets on port 22 if a new connection is associated with an already established connection.
-A INPUT -p tcp –dport 22 -m state –state NEW,ESTABLISHED -j ACCEPT






 SolarWinds Hack and Supply-Chain Attack Demystified.
SolarWinds Hack and Supply-Chain Attack Demystified.





